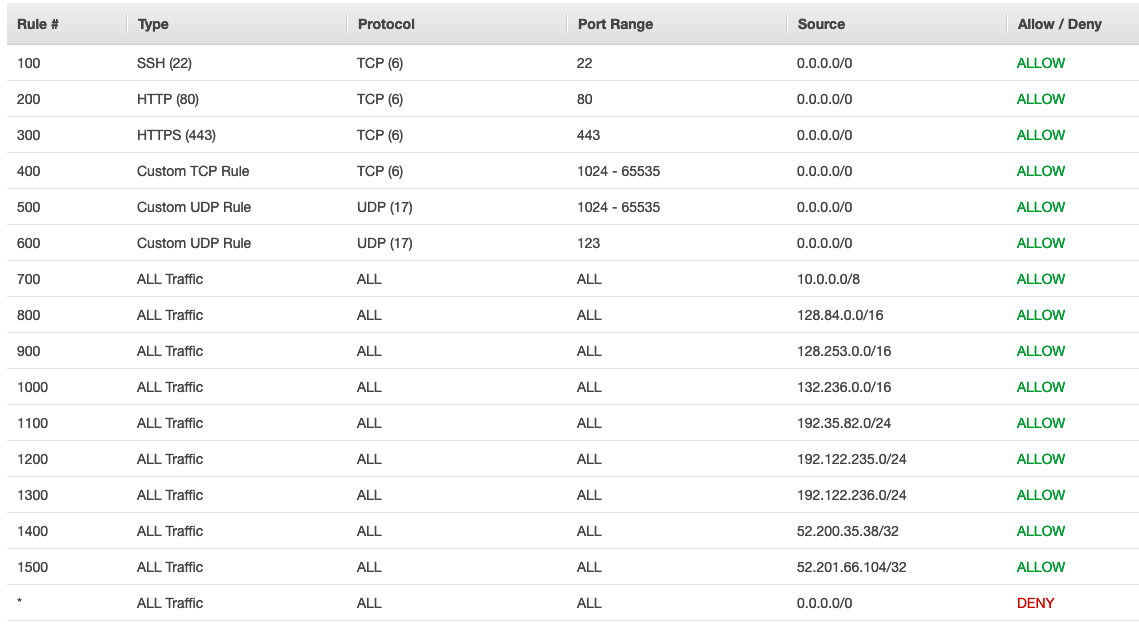
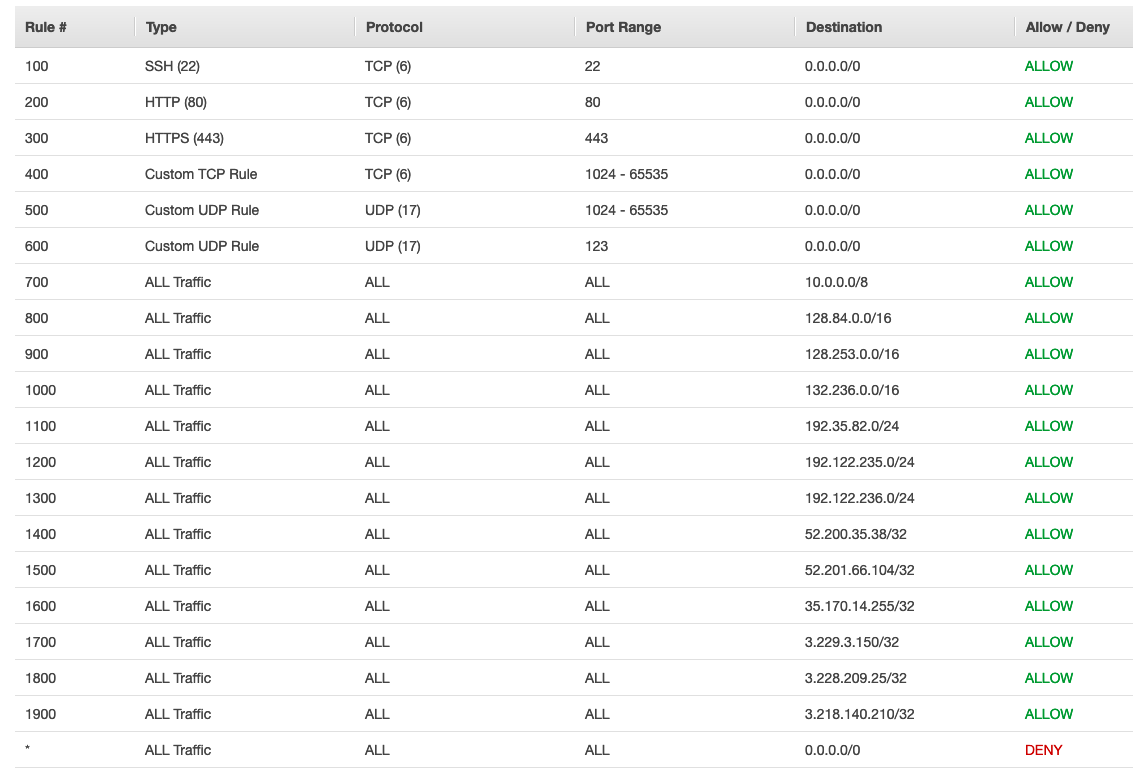
This network ACL is the recommended baseline for AWS VPC subnets. It should be configured and used on all AWS VPC subnets. You are welcome to make your NACL more stringent, but we recommend careful consideration before making it less stringent.
Important IPs and CIDR Blocks
These IPs and CIDR blocks are referenced in the Baseline NACL:
| CIDR | DNS Name | Description |
|---|---|---|
| 52.200.35.38/32 | kerberos-aws.login.cornell.edu | AWS-based Cornell Kerberos Server |
| 52.201.66.104/32 | kerberos-aws2.login.cornell.edu | AWS-based Cornell Kerberos Server |
| 128.84.0.0/16 | Cornell campus public IPs | |
| 128.253.0.0/16 | Cornell campus public IPs | |
| 132.236.0.0/16 | Cornell campus public IPs | |
| 192.35.82.0/24 | Cornell campus public IPs | |
| 192.122.235.0/24 | Cornell campus public IPs | |
| 192.122.236.0/24 | Cornell campus public IPs | |
| 35.170.14.255/32 | test.directory.cornell.edu | AWS-based TEST directory |
| 3.229.3.150/32 | test.directory.cornell.edu | AWS-based TEST directory |
| 3.228.209.25/32 | query.directory.cornell.edu | AWS-based PROD directory |
| 3.218.140.210/32 | query.directory.cornell.edu | AWS-based PROD directory |
CloudFormation
A CloudFormation template to create a Network ACL for with the baseline rules can be found here: https://github.com/CU-CommunityApps/cu-aws-cloudformation/tree/master/baseline-nacl
Manual Configuration
Inbound Rules
Outbound Rules