Sharing your calendar with your co-workers has been discussed in a past blog post (click here to view it). But what about when you want to share your calendar with someone outside of Cornell?
When I looked into this a few years ago, the only option I could find was to send the outsider a ‘snap shot’ of your calendar (unless you got fancy and started linking your Exchange calendar with a Google calendar). With the ‘snap shot’, it meant that whatever was listed in your calendar when you sent it was what they could see – no later updates or additions, unless you sent them another ‘snap shot’.
I had someone recently ask again about being able to do this, and found that there is a way for you to publish your real-time calendar through Outlook or OWA (exchange.cornell.edu), so I thought I’d share since it could be very beneficial to those of you that work with outside organizations.
Here’s how: http://help.outlook.com/en-US/140/ms.exch.ecp.CalendarPublishing.aspx
Please note these choices for published calendars:
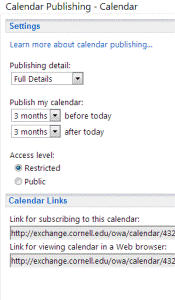
- You can select how much detail can be viewed on your published calendar: Availability Only, Limited Details or Full Details
(Even if you select Full Details, those appointments set as ‘private’ will not be shared.) - You can restrict how many months before and after today’s date to publish.
- You have two options for access: Restricted or Public.
- Restricted means that the only way a person would be able to view your calendar is if they knew the web link to your published calendar.
- Public allows anyone to search for your calendar on the Internet (I would only recommend this for a group account calendar where you have only public events you wish to advertise)
Click here for an example of a published Exchange calendar - You will have two web links that you can copy and paste to send to the outsider. (See photo)
- ‘Link for subscribing…’ is a ics file which means the person will be able to view your calendar in Outlook.
- ‘Link for viewing..’ is a html web address for the person to view your calendar in their web browser (see example link above)
Keep in mind that after the e-mail/calendar switch to Office365 early next year, the link to your published calendar will change.
You’ve all heard these terms, especially from me when warning of the latest unsafe e-mail that could be in your Inbox. I sent out a notice yesterday about an e-mail with an attached virus and there is another e-mail that you need to delete going around today with the subject “Confidential - Secure Message from AMEX”.
So what exactly do these terms mean?
Spam is the use of e-mail to send unsolicited bulk messages, especially for advertising, indiscriminately. (Think of the unsolicited calls you get at home asking you to buy product X, they aren’t necessarily trying to steal your information but they are trying to get you to buy something.)
- A common question asked to me is ‘how do they get my e-mail address?’. Read this article about ‘How Spam Works’: http://computer.howstuffworks.com/internet/basics/spam.htm
Phishing is the act of attempting to acquire information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication.
- A great example of this is the common e-mail that looks like it’s coming from the IT department stating “Your Inbox is nearly full!!! Send us your username and password now to fix this…” There may be no clickable web link or attached virus that will run on your computer, it’s simply attempting to have someone reply back with their information.
Malware, short for malicious (or malevolent) software, is software used or created by attackers to disrupt computer operation, gather sensitive information, or gain access to private computer systems. Malware includes computer viruses, worms, trojan horses, spyware, adware, and other malicious programs.
- The term computer virus is used for a program that has infected some executable software and, when run, causes the virus to spread to other software. Viruses can be transmitted as attachments to an e-mail note or in a downloaded file, or be present on a usb drive or CD. Some viruses wreak their effect as soon as their code is executed; other viruses lie dormant until circumstances cause their code to be executed by the computer. Some viruses are benign or playful in intent and effect ("Happy Birthday, Ludwig!") and some can be quite harmful, erasing data or causing your hard disk to require reformatting.
- A worm is a program that actively transmits itself over a network to infect other computers. (Which is why we ask that you remove your computer immediately from the network when you know or suspect you have some type of malware on your computer.)
There is no such thing as being too cautious with your email, and please don’t ever hesitate to ask your local IT contact or me if you question a particular email. (An ounce of prevention is worth a pound of cure… Sorry, I had to use that saying since I just heard it again yesterday and it’s stuck in my head when thinking of these e-mails. For anyone that’s fallen victim to one and has had to deal with the consequences, you’ll understand completely! -- Dealing with identity fraud or having to wait to use your computer again while Windows is reinstalled is never fun.)
Set Up A Scheduled Symantec Anti-virus Scan
Make sure your Symantec program is running at least a weekly scan to check for malware on your computer. Here’s how to set it up: http://screencast.com/t/NFdAvKQof
For information, see my blog post from August about these suspicious e-mails.