This document describes the procedure used to install Shibboleth Service Provider (SP) software on Windows Server and Internet Information Server (IIS), and to configure it to work with the Cornell Shibboleth Identity Provider (IdP).
These links may break at some point, but for now the 32-bit and 64-bit run times can be found at:
The top-level link to find them is https://visualstudio.microsoft.com/downloads/ via Other Tools.
2.1 Download the latest version of the Windows installer package from the Shibboleth download site at https://shibboleth.net/downloads/service-provider/latest/. Select either the win32/ or win64/ directory as appropriate to your 32-bit or 64-bit system. Then download .msi file.
2.2 Run the installer package. It is recommended that you accept all defaults, as follows:
On the Administrative Tools menu, click Services. Find Shibboleth Daemon in the list and double-click it. Verify that Service Status is "Running", Startup type is "Automatic", and on the Log On tab, verify that "Local System" is selected.
Go to your SP installation directory(C:\opt\shibboleth-sp if you use the default) . All the SP configuration files are in the \etc\shibboleth directory.
Save a copy of attribute-map.xml to attribute-map.xml.orig or similar. Download our sample attribute-map.xml and replace your attribute-map.xml with downloaded file. Our attribute-map.xml defines all commonly used attributes. All attributes except groups are released by default to all SP. Attribute "groups" is released on demand. Submit group membership requirement when you submit shibboleth integration request form. Find all the default attributes released by Cornell IDP from Shibboleth at Cornell Page. Edit attribute-map.xml as needed |
Save a copy of
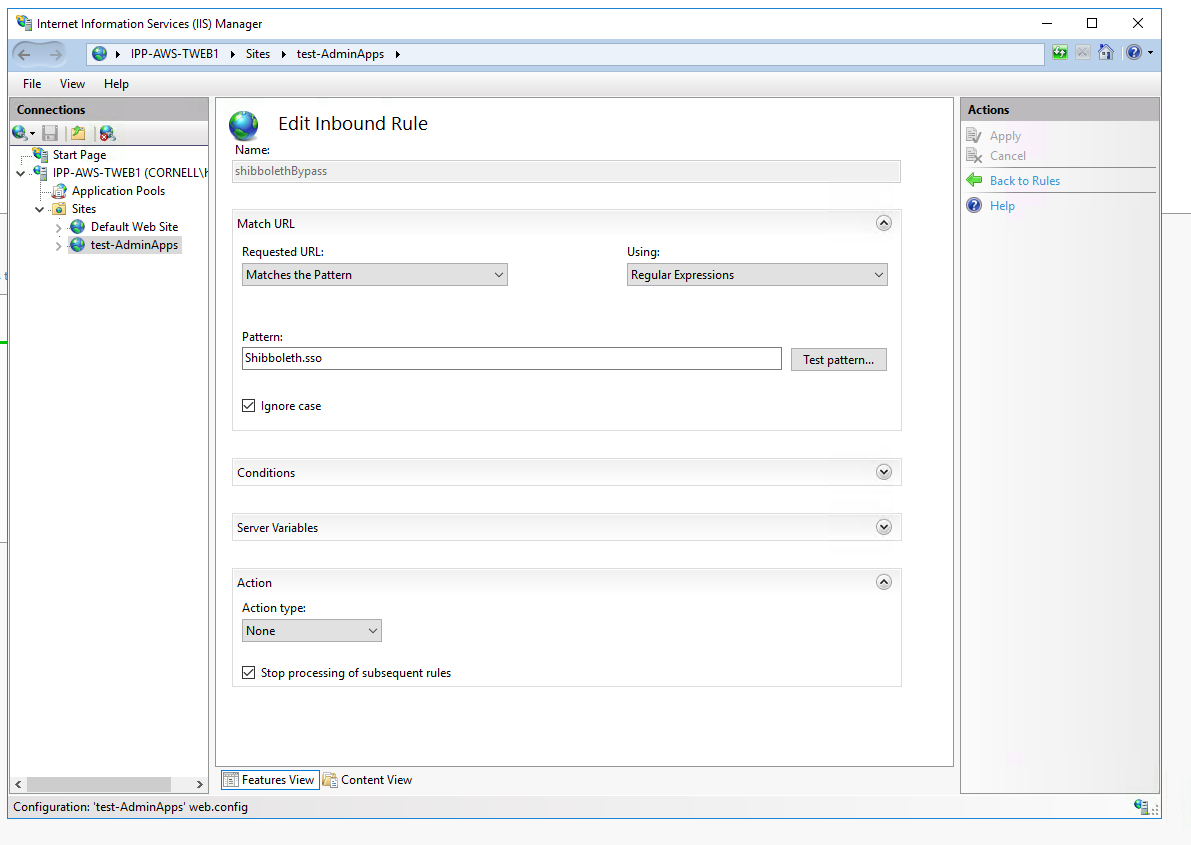
Find <ISAPI...>...<Site id="1" name="shibtest.cit.cornell.edu"/>. Change the "site id" to match the id assigned to your site by IIS. You can find your site id in Internet Services (IIS) Manager by clicking on "Sites". In this same location, change the site name to your DNS name. Our example defined two sites. Delete or add more as needed.
Find <RequestMap>...<Host name="shibtest.cit.cornell.edu">. Change the "Host name" to the site name you defined in step above. In our example files, we defined two hosts and specifies different authorization rules for each site and location. Please modify it to meet your site requirement. Additional resources for AccessControl: https://wiki.shibboleth.net/confluence/display/SP3/XMLAccessControl
Find <ApplicationDefaults entityID="shibtestsites.cit.cornell.edu" ...>. Change the "entityID" to whatever you like. EntityID is the name of your SP and should be unique. We recommend you include domain name in entityID to guarantee it is unique. It's better not include space or special characters in it( / or : are fine).
Find < Errors supportContact ="root@localhost" helpLocation ="/about.html" styleSheet ="/shibboleth-sp/main.css" />. Change the email address to your application's support email address.
|
3. Verify the Configuration
Go to your SP installation directory(default C:\opt\shibboleth-sp), cd to /sbin64 or /sbin directory as appropriate to your 64-bit or 32-bit system. Running the code below from the command line:
shibd.exe -check |
If the last line of the output is the following message, everything is as expected:
"overall configuration is loadable, check console fornon-fatal problems"If there is error, check log for detail. All the log files are in SP installation directory\var\log\shibboleth
4. Install X509 Certificate
As Shibboleth requires a certificate and key to encrypt and decrypt attribute assertions, an X509 certificate must be installed for it to work. Now that the shibboleth2.xml file has been updated, use the keygen.bat command in C:\opt\shibboleth-sp\etc\shibboleth to create new certificates with the hostname(server name) and entityID. Use the following format:
keygen.bat -h idmwebserver.cit.cornell.edu -e entityID -y number of years to issue |
where the values for each are substituted accordingly
keygen.bat -h idmwebserver.cit.cornell.edu -e shibtestsites.cit.cornell.edu -y 10 |
The 10 indicates the number of years for which the certificate is issued. You may specify a different value.
Restart IIS and the Shibboleth Daemon. The Shibboleth Daemon can be restarted using the Administrative Tools > Services navigation.
Navigate to https://yoursiteDomain/Shibboleth.sso/Metadata and download it. Open your downloaded file with text editor. Make sure the entityID is the same as your defined in shibboleth2.xml. If there are multiple sites in IIS require Shibboleth authentication and you define them in shibboleth2.xml, you need to manually add consumer service url for each site in your SP's metadata.
For example, I get my SP's metadata from https://shibtest.cit.cornell.edu/Shibboleth.sso/Metadata, in the metadata there should be a line like this:
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://shibtest.cit.cornell.edu/Shibboleth.sso/SAML2/POST" index="1"/>
I also have shibtest1.cit.cornell.edu defined in shibboleth2.xml, I need to add AssertionConsumerService url for shibtest1.cit.cornell.edu like this
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://shibtest1.cit.cornell.edu/Shibboleth.sso/SAML2/POST" index="2"/>
Save your metadata file. You'll need to submit your SP's metadata in shibboleth integration request form.
If your site is configured with test IDP, you don't have to submit Shibboleth integration request form because test IDP supports anonymous SP. You can start testing the authentication of your site.
For sites configured with prod IDP, submit your shibboleth integration request from https://shibrequest.cit.cornell.edu. On the second page of request form, select 'No' for question "Has the application service provider's metadata been published with InCommon?". Use text editor open your SP's metadata, copy the content of the metadata and paste it in the request form.Once the form is submitted, Identity Management get a Remedy case. We'll configure your SP in prod IDP in 1 - 2 business day. We'll notify you when the configuration is complete.
Confirm that you are able to log in with your netID and that attributes are properly released.
contact idmgmt@cornell.edu