This page shows and discusses the different routing options over the Cornell Direct Connect to AWS VPCs. |
| Term | Definition |
|---|---|
| Asymmetric Routing | Condition that presents itself when network traffic between a client and its destination follows different paths inbound and outbound. This results in the client sending packets to one IP address but receiving responses from a potentially different IP address, preventing client and server from properly establishing two-way communication. |
| AWS Private Subnet | Subnet in an AWS VPC that has no direct access to the Internet. |
| AWS Public Subnet | Subnet in an AWS VPC that has direct Internet access by way of a configured Internet gateway (IGW). |
Cornell Private Network | Private IPv4 address range 10.0.0.0/8, defined in RFC 1918 for use on private/internal networks. Addresses in this range are not allowed to leave the Cornell network and route directly over the Internet. |
| Cornell Public Network | Cornell's publicly routable IPv4 address ranges. |
| Direct Connect | Dedicated network connection between Cornell and Amazon Web Services via AWS peering partners. Direct Connect should be treated as if it were a campus network, including leveraging transport encryption for sensitive data. See also Cornell AWS Direct Connect. |
| Internet Gateway (IGW) | AWS-managed VPC routing device that provides inbound and outbound access from a subnet to the Internet. Allows use of public IP addresses (Elastic IP) on EC2 Instances. |
| Transit Gateway (TGW) | AWS-managed routing device that can cross-connect VPCs and Direct Connect resources. Transit Gateways are an integral component in the Cornell AWS Direct Connect Architecture. |
| Direct Connect Gateway (DCGW) | AWS-managed routing device that can connect VPCs and Transit Gateways in multple regions to Direct Connect connections. Direct Connect Gateways are an integral component in the Cornell AWS Direct Connect Architecture. |
| TCGW-DCGW infrastructure | The infrastructure components in the Cornell AWS Direct Connect Architecture that lie between the campus network and an AWS VPC using Direct Connect. |
| Secondary CIDR (in VPCs) | The secondary CIDR block is an extra, small CIDR block added to VPCs for use by the TGW-DCGW infrastructure. This CIDR block should not be used for any purpose other than for utility subnets. |
| Utility Subnets | Utility subnets are small ( |
The discussion and examples below focus on traffic between private and public network segments in AWS, and private and public network segments on campus. Although the Cornell AWS Direct Connect Architecture also links AWS VPCs to Cornell's private network segments in Azure, traffic between AWS and Azure is not included in this article.
This is the preferred routing configuration for VPCs that have no specific requirements to directly address Cornell Public Network addresses via Direct Connect. It is the easiest to understand and troubleshoot.
In this configuration, the Cornell campus network will route network traffic to the VPC's private address space over the Direct Connect. The DCGW+TGW infrastructure connected to the AWS VPC will route any Cornell Private Network traffic not destined for Cornell VPCs in AWS back to the Cornell campus network via Direct Connect. This effectively leverages the Direct Connect as an extension of the Cornell Private Network.
Traffic from the VPC destined for other Cornell AWS VPCs will transit the DCGW+TGW infrastructure or dedicated peering connections, without exiting AWS.
When using the Private Network Extension model:
In the diagram below, Client 2 (Cornell Public Network) and Client 3 (Internet User) cannot reach Service A or Service B via their Cornell Private Network (10.0.0.0/8) addresses without use of a Cornell departmental VPN. Leveraging a Cornell departmental VPN connection would give either client an IP address and routing configuration for Cornell Private Network space, allowing them to directly contact the private IP addresses of Service A and Service B. This configuration is not shown in the diagram.
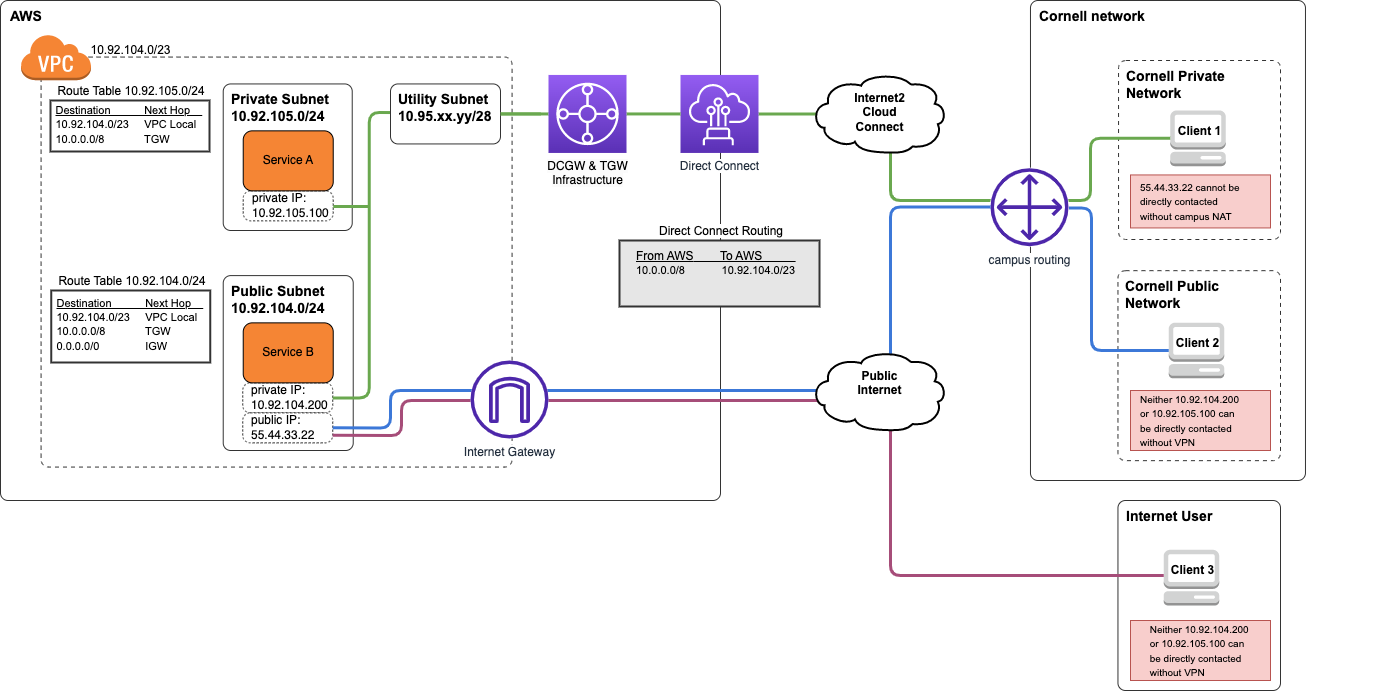
draw.io source: private-network-extension.v2.drawio
This is our preferred routing configuration for VPCs that have a requirement for AWS Private Subnets to directly address Cornell Public Network addresses via Direct Connect.
In this configuration, the Cornell campus network will route network traffic to the VPC's private address space over the Direct Connect. The DCGW+TGW infrastructure connected to the AWS VPC will route traffic from Private AWS subnets to both Private and Public Cornell network segments back to campus via Direct Connect. For Public AWS subnets, the DCGW+TGW infrastructure will route traffic only to Private Cornell network segments back to campus via Direct Connect.
As in the Private Network Extension configuration discussed earlier, local VPC traffic (i.e. destined for the VPC itself), traffic to peered AWS VPCs, and traffic to other Cornell VPCs using Direct Connect in AWS remains within AWS and is not sent back to campus over the Direct Connect.
To prevent asymmetric routing from occurring, this configuration leverages a distinct set of routing tables in the AWS VPC for Public and Private subnets.
When using the Hybrid Routing model:
In the diagram below:
Leveraging a Cornell departmental VPN connection would give either client an IP address and routing configuration for Cornell Private Network space, allowing them to directly contact the private IP addresses of Service A and Service B. These configurations are not shown in the diagram.
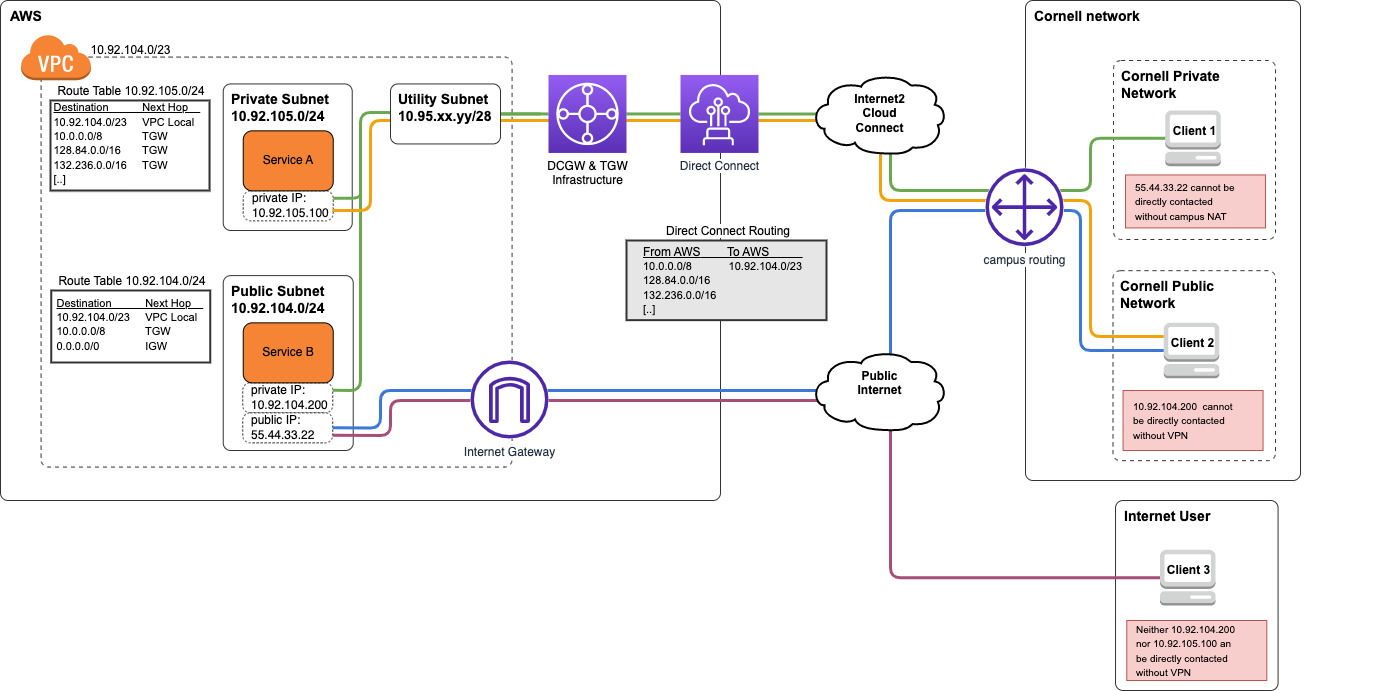
draw.io source: hybrid-routing.v2.drawio
This configuration, though similar to Hybrid Routing, is not preferred since it allows for the possibility of asymmetric routing on AWS Public Subnets. Given the similarity to Hybrid Routing and the potential to serve similar use cases, we strongly recommend against using this option.
In this configuration, the Cornell campus network will route network traffic to the VPC's private address space over the Direct Connect. The DCGW+TGW infrastructure connected to the AWS VPC will route traffic from both Private and Public AWS subnets to both Private and Public Cornell network segments back to campus via Direct Connect.
As in the Private Network Extension and Hybrid Routing configurations discussed earlier, local VPC traffic (i.e. destined for the VPC itself), traffic to peered AWS VPCs, and traffic to other Cornell VPCs using Direct Connect in AWS remains within AWS and is not sent back to campus over the Direct Connect.
There is no inherent protection against asymmetric routing from occurring as all advertised routes from Cornell campus are presented in the subnet routing tables.
When using the "All Campus" Routing model:
In the diagram below:
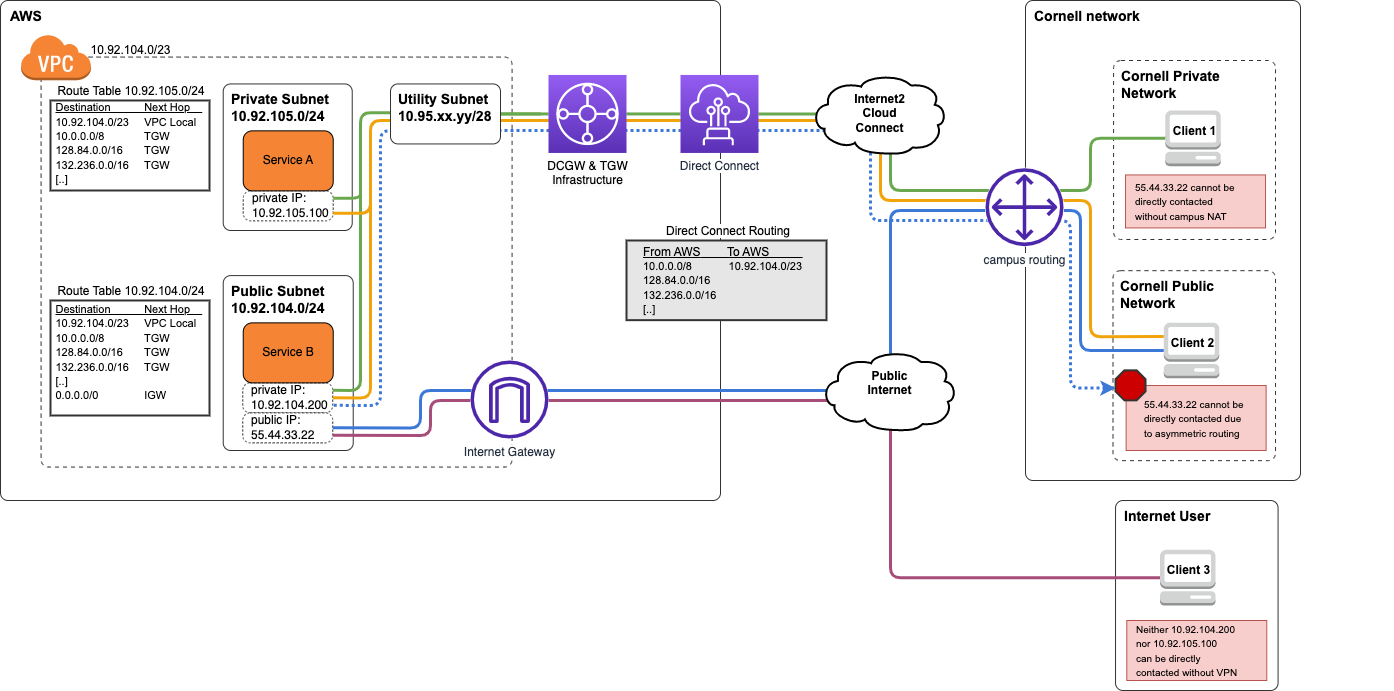
draw.io source: all-campus-routing.v2.drawio
The examples below shows the VPC using Direct Connect as having 10.92.104.0/23 as primary CIDR and 10.95.32.0/26 as secondary CIDR (used for utility subnets).
| Destination | Target | |
|---|---|---|
| 0.0.0.0/0 | NAT Gateway | public internet |
| 10.92.104.0/23 | local | primary VPC CIDR |
| 10.95.32.0/26 | local | secondary VPC CIDR |
| 10.0.0.0/8 | TGW | Cornell private CIDR |
| Destination | Target | |
|---|---|---|
| 0.0.0.0/0 | IGW | public internet |
| 10.92.104.0/23 | local | primary VPC CIDR |
| 10.95.32.0/26 | local | secondary VPC CIDR |
| 10.0.0.0/8 | TGW | Cornell private CIDR |
| Destination | Target | Notes |
|---|---|---|
| 0.0.0.0/0 | NAT Gateway | public internet |
| 10.92.104.0/23 | local | primary VPC CIDR |
| 10.95.32.0/26 | local | secondary VPC CIDR |
| 10.0.0.0/8 | TGW | Cornell private CIDR |
| 128.84.0.0/16 | TGW | Cornell public CIDR |
| 128.253.0.0/16 | TGW | Cornell public CIDR |
| 132.236.0.0/16 | TGW | Cornell public CIDR |
| 192.35.82.0/24 | TGW | Cornell public CIDR |
| 192.122.235.0/24 | TGW | Cornell public CIDR |
| 192.122.236.0/24 | TGW | Cornell public CIDR |
| Destination | Target | |
|---|---|---|
| 0.0.0.0/0 | IGW | public internet |
| 10.92.104.0/23 | local | primary VPC CIDR |
| 10.95.32.0/26 | local | secondary VPC CIDR |
| 10.0.0.0/8 | TGW | Cornell private CIDR |
| Destination | Target | Notes |
|---|---|---|
| 0.0.0.0/0 | NAT Gateway | public internet |
| 10.92.104.0/23 | local | primary VPC CIDR |
| 10.95.32.0/26 | local | secondary VPC CIDR |
| 10.0.0.0/8 | TGW | Cornell private CIDR |
| 128.84.0.0/16 | TGW | Cornell public CIDR |
| 128.253.0.0/16 | TGW | Cornell public CIDR |
| 132.236.0.0/16 | TGW | Cornell public CIDR |
| 192.35.82.0/24 | TGW | Cornell public CIDR |
| 192.122.235.0/24 | TGW | Cornell public CIDR |
| 192.122.236.0/24 | TGW | Cornell public CIDR |
| Destination | Target | Notes |
|---|---|---|
| 0.0.0.0/0 | IGW | public internet |
| 10.92.104.0/23 | local | primary VPC CIDR |
| 10.95.32.0/26 | local | secondary VPC CIDR |
| 10.0.0.0/8 | TGW | Cornell private CIDR |
| 128.84.0.0/16 | TGW | Cornell public CIDR |
| 128.253.0.0/16 | TGW | Cornell public CIDR |
| 132.236.0.0/16 | TGW | Cornell public CIDR |
| 192.35.82.0/24 | TGW | Cornell public CIDR |
| 192.122.235.0/24 | TGW | Cornell public CIDR |
| 192.122.236.0/24 | TGW | Cornell public CIDR |