...
STS Token use for manual data transfers with existing shibboleth IAM roles
There are some options here:
- Install the aws login tool (Access Keys for AWS CLI Using Cornell Two-Step Login (Shibboleth)
- Docker with the aws login tool with other helpful cloud utilities (https://github.com/CU-CommunityApps/ct-cloud-utils-dockerized)
- Install the aws cli (https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-install.html) using 'aws sts get-session-token' with a new or existing IAM user (https://docs.aws.amazon.com/cli/latest/reference/sts/get-session-token.html)
- Create a new or use default profile
- "aws configure --profile {name}"
- AWS CLI
- rclone
- rclone config
- set id, secret and session token (under advanced config)
- rclone config
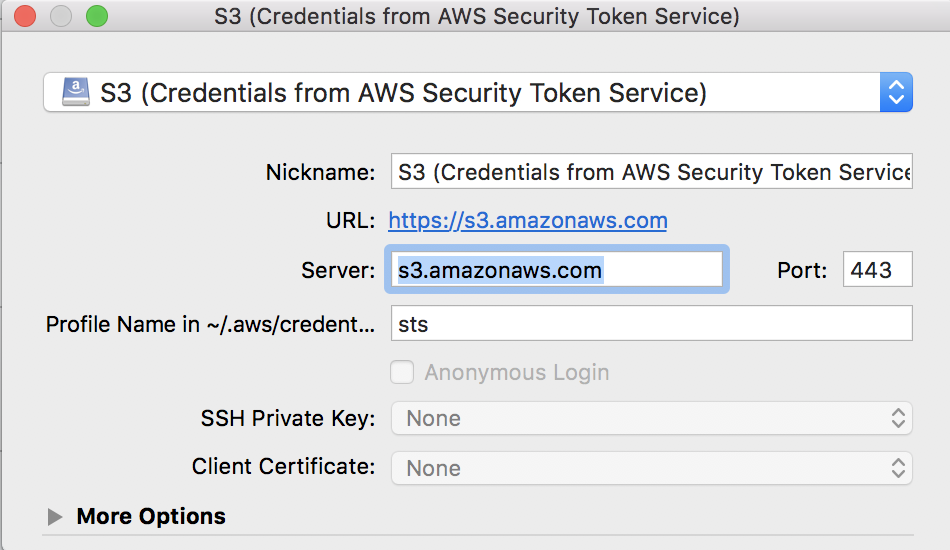
- Cyberduck Cyberduck
- Create sts profile in ~/.aws/credentials file"aws configure --profile sts" and/or text editor
- Copy ID, Secret and Token from ~/.aws/credentials {name}
- from https://signin-sts.aws.cucloud.net
- aws_access_key_id = [ paste ID ]
- aws_secret_access_key = [ paste key ]
- aws_session_token = [ paste token ]
[sts] - Download Cyberduck STS token profile
- Open Connection - S3 (Credentials from AWS Security Token Service)
- Specify profile from #1
- Specify profile from #1
- Copy ID, Secret and Token from ~/.aws/credentials {name}
- Mountain Duck now available with similar process as outlined above with CyberDuck.
...