...
- Basic auditing configurations (i.e., CloudTrail, AWS Config)
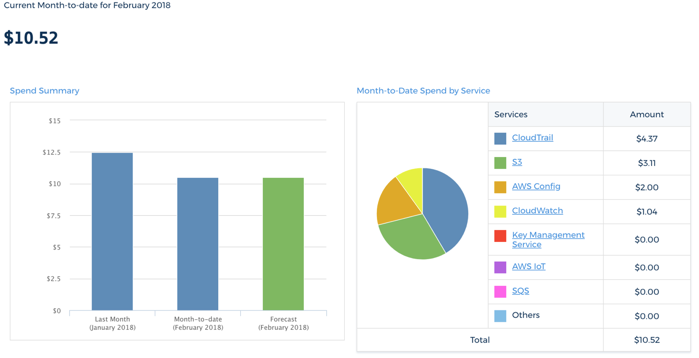
- This costs in the ballpark of about $10/month, even if you aren't actively using the AWS account.
Graph of Typical Costs for auditing configurations
Expand
- This costs in the ballpark of about $10/month, even if you aren't actively using the AWS account.
- Cornell standard VPC and it's its associated NAT gateway
- This costs in the ballpark of about $40/month, even if you aren't actively using the AWS account. A big part of that is the NAT gateway which costs about $1/day.
- You will see this baseline cost only if the Cloud Team has configured a Cornell Standard VPC. AWS accounts used for research generally don't have a Cornell Standard VPC configured.
...
AWS offers a Data Egress Waiver that mostly eliminates Data Transfer charges for Cornell. See the AWS blog post about it for more details.
Is
...
egress from all AWS offerings covered by the waiver?
As of February 2018, most services that advertise the $0.09/GB data egress fee on the pricing page are covered. Feel free to check with the Cloud Team if you aren't sure about a particular service.
A notable exception is currently CloudFront egress, which is not covered by the waiver. CloudFront egress shows as a separate line-item and is billed at a (slightly) cheaper rate than normal data egress. AWS is currently looking into adding CloudFront egress to the waiver. Any campus customers who currently have a current or future plan to generate significant CloudFront egress charges should forward their use-case to the Cloud Team for a consult with our AWS Representatives.
...
In most cases, the EC2 charge you are seeing is a result of the standard configuration we use in your VPC. The private subnets in your Cornell standard VPC are connected to the world (for outgoing traffic) by a NAT instancegateway. That NAT instance gateway is really a small EC2 instance, though it won't appear in your EC2 instance list in the AWS Console. You can see the NAT instancegateway(s) configured for your account here: https://console.aws.amazon.com/vpc/home?region=us-east-1#NatGateways:sort=desc:createTime
The NAT instance gateway gives EC2 instances in your private subnets access to the world for things like Linux repos , or Windows update servers. We do have some AWS account owners that do not find the $1/day cost of the NAT gateway to be worthwhile and turn it off. However, we caution about We advise caution around this because, with it off, your instances will not be able to do something as basic and critical as running "yum update" or "apt-get update" or get Windows updates.
Contact the Cloud Team if you'd rather not have the NAT gateway deployed for that VPC.
See NAT Gateway gateway pricing info here: https://aws.amazon.com/vpc/pricing/.
...
Until direct billing is turned on, you can use the CloudCheckr website or our billing API to sub-total the resource costs in your account (based on tag) and re-allocate those costs with the help of your unit Business Service Center.
...
No. Our Shibboleth implementation does not work with DOC accounts, Holding IDs, or Guest IDs. (More info about various Cornell account types: https://it.cornell.edu/cornellad/terms-and-conditions-cornellad and Cornell's Shibboleth Implementation. Please )
Please contact cloud-support@cornell.edu to discuss other options.
...
In the majority of other scenarios, the Cloud Team recommends using the public internet to transfer all data and updating firewall configurations to allow access to/from the internet with trusted systems that you run in AWS. The available bandwidth to the internet is much greater than when using the thin 1Gbps Direct Connect that is shared among many units at Cornell.
...