...
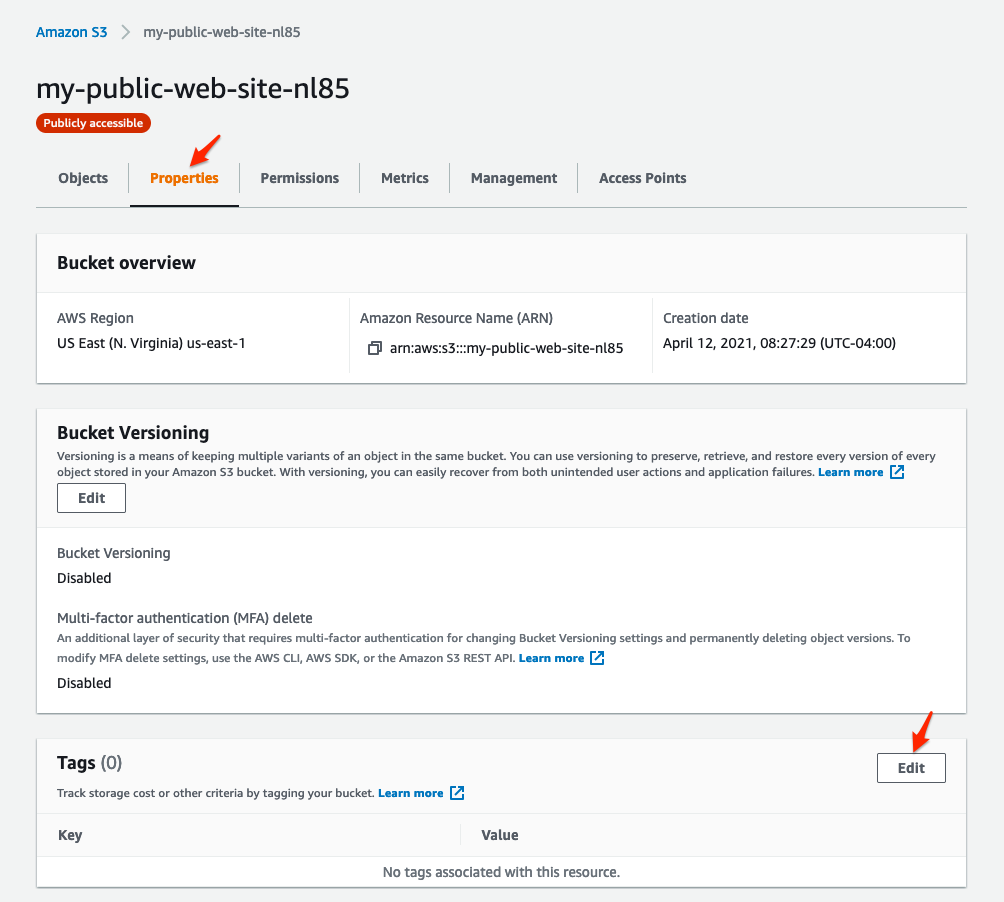
- In the S3 console, with "your" bucket selected, click on the Properties tab and scroll down to Tags.
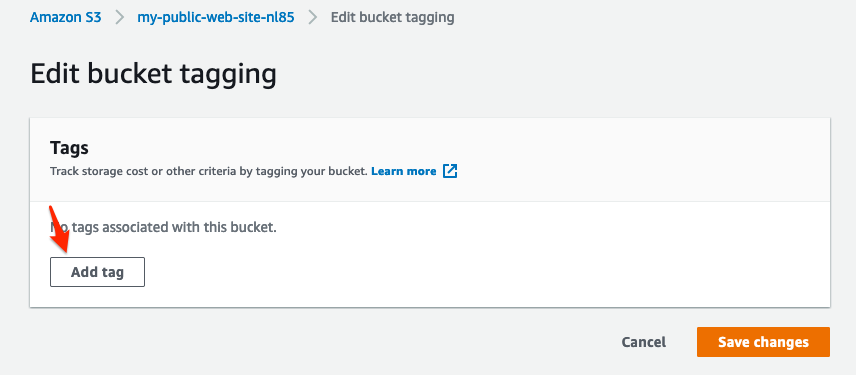
- Click Edit in the tags section.
- Click on Add tag.
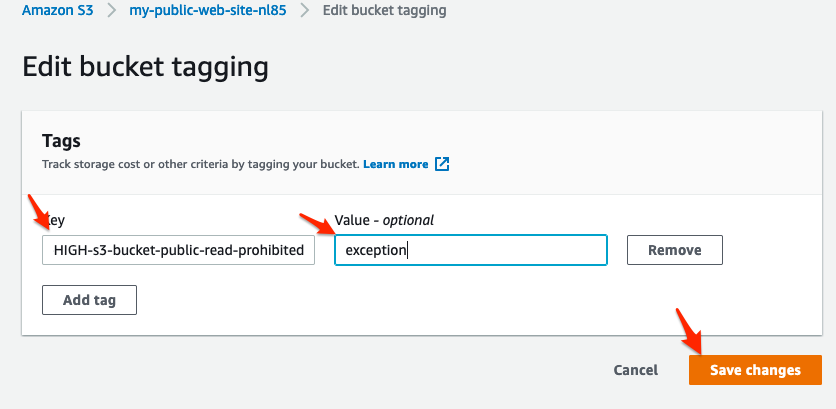
- Add a tag with the following details, and click on Save changes:
- Key: cit:config:153-HIGH-s3-bucket-public-read-prohibited
- Value: exception
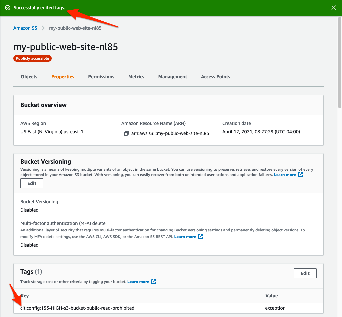
- On resulting bucket Properties page confirm that your new tag is shown as one of the bucket tags.
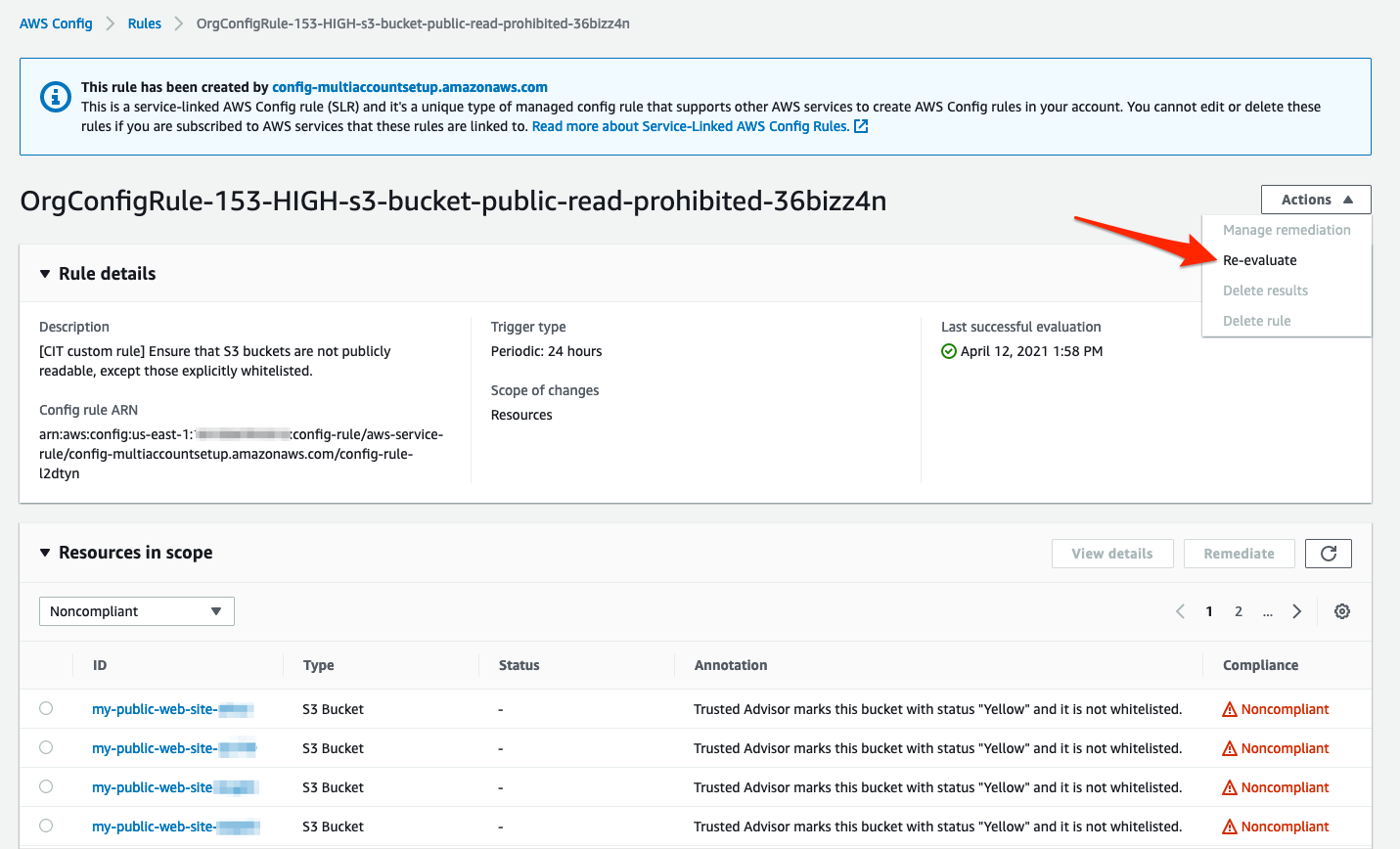
Part 3 – Wait for Config Rule re-evaluation
...
- In all likelihood one, if not both, of "your" resources remain flagged as non-compliant.
- One reason for this is that Config evaluations operate on snapshots of resource configurations, not from an instantaneous reading of the resource details.
- Another factor that seems to come into play is that Config evaluation results themselves are cached and sometimes you may be looking at results from the previous evaluation.
- The secret for maintaining your sanity with Config is to check back with Config for new results on the day after you make resource configuration changes. What you see after 24 hours is typically a meaningful set of results.
| Info |
|---|
If you wanted to force Config to evaluate a Rule within your own AWS account, you would use the Re-evaluate action, as shown below. |